Encryption is the process by which a readable message is converted to an unreadable form to prevent unauthorized parties from reading it. Decryption is the process of converting an encrypted message back to its original (readable) format. The original message is called the plaintext message. The encrypted message is called the ciphertext message.
Digital encryption algorithms work by manipulating the digital content of a plaintext message mathematically, using an encryption algorithm and a digital key to produce a ciphertext version of the message. The sender and recipient can communicate securely if the sender and recipient are the only ones who know the key.
Shared Key and Public Key Encryption
SKIP uses a combination of shared key cryptography and public key cryptography to protect messages sent between hosts. SKIP hosts use shared traffic keys that change frequently to encrypt data sent from one host to another. To protect these shared traffic keys, SKIP hosts use the public key to calculate an implicit shared secret, which they use to encrypt the shared traffic keys, keeping network communication secure.
Shared Key Encryption
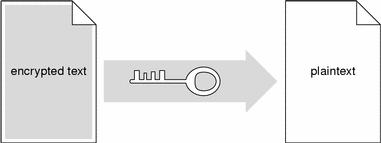
Shared key encryption uses one key to encrypt and decrypt messages. For shared key cryptography to work, the sender and the recipient of a message must both have the same key, which they must keep secret from everybody else. The sender uses the shared key to encrypt a message, shown in the following figure, and then sends the ciphertext message to the recipient.
Figure B-1 Sender Uses Key to Encrypt Plaintext to Ciphertext
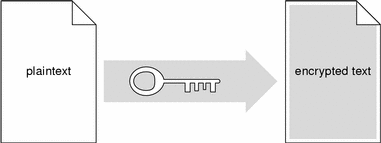
When the ciphertext message arrives, the recipient uses the identical shared key to decrypt the message, shown in the following figure.
Figure B-2 Recipient Uses Key to Decrypt Ciphertext to Plaintext
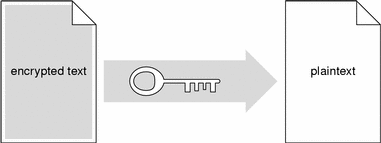
Shared key encryption/decryption is relatively fast. However, since anyone with the shared key can decrypt the information, shared key encryption requires that only the sender and recipient have access to the shared key. SunScreen SKIP uses shared key algorithms to encrypt packets sent between hosts. SunScreen SKIP protects the security of encrypted information by generating new traffic keys frequently during a communication session, making acquisition of any one traffic key useless.
Public Key Encryption
Public key encryption uses a pair of complementary keys (a public key and a private key) to encrypt and decrypt messages, as shown in the following figure. The two keys are mathematically related such that a message encoded with one key can only be decoded with the other key. Although a user's public and private keys are mathematically related, knowledge of a public key does not make it possible to calculate the corresponding private key.
Figure B-3 Complementary Public and Private Keys
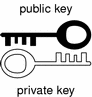
In public key encryption systems, users make their public key available to anyone and keep their private key secret. When one user wants to send a private message to another user, the sender looks up the recipient's public key and uses it to encrypt a message, as shown in the following figure, before sending it to the recipient.
Figure B-4 Sender Uses Recipient's Public Key to Encrypt Message
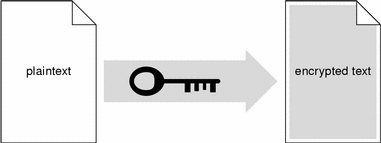
When the encrypted message arrives, the recipient uses his or her private key to decrypt the message, shown in the following figure. Because the recipient's private key is known only to the recipient, both the sender and recipient can safely assume that no one other than the recipient can read the message.
Figure B-5 Recipient Uses Private Key to Decrypt Message
Public key encryption algorithms are mathematically more complex than shared key encryption algorithms. As a result, public key encryption is significantly slower than shared key encryption. Consequently, SunScreen SKIP uses Diffie-Hellman key pairs (described in the next section) to create a shared secret between two users, and then uses shared key encryption to encrypt traffic traveling between the two hosts.
Diffie-Hellman Key Exchange
The Diffie-Hellman key exchange algorithm, which is named after its inventors, solves the problem of securely distributing keys by removing the need to transmit secret keys. When two hosts wish to use the Diffie-Hellman algorithm to exchange keys, they agree to use the same numerical values for the key basis (g) and modulus (p). Each host generates a large (512-, 1024-, or 2048-bit) random number (x) as a private key, and then uses this private key to generate a public key gx mod p.
Once a user's private and public keys have been calculated, SunScreen SKIP creates the user's public certificate. This certificate contains the public key value, the g and p values used to compute the public key, and other information, such as the period for which the certificate is valid.
SunScreen SKIP hosts exchange their public certificates with one another freely. When two hosts wish to communicate securely, each host calculates a mutually authenticated shared secret based solely on knowledge of its private key and the other host's public key.
For example, host I would select a random number i as a private key and then generate a public key gi mod p. Similarly, host J would select a random number j as a private key and then generate a public key gj mod p. The two hosts then exchange their public keys over secure or insecure links. Host I raises J's public key (gj mod p) to the power of its private key i, yielding (gj)i mod p or gji mod p. Host J raises I's public key (gi mod p) to the power of its private key j, yielding (gi)j mod p or gij mod p. Consequently, hosts I and J can derive a mutually authenticated long-term secret gij mod p implicitly (without explicit communication). Since no one other than I and J have access to their private keys, no one other than I and J can compute gij mod p.
The two hosts then take the low-order bits of gij mod p to derive a pairwise master key Kij. Kij is an implicit shared master key that does not need to be sent in any packet or negotiated out of band.
In theory, the two hosts could use their shared master key Kij to encrypt messages. However, doing so might expose Kij to analysis and eventual decryption. Instead, SunScreen SKIP uses a rapidly-changing series of traffic keys to encrypt messages traveling between the two hosts, and uses a modified version of Kij to encrypt these traffic keys. See "Perfect Forward Secrecy", below, for more information.
Perfect Forward Secrecy
Perfect forward secrecy substitutes a clock-based master key for the long-term Diffie-Hellman shared secret Kij. Using a clock-based master key means that the long-term secret Kij is never directly exposed to third parties, making it less vulnerable to cryptanalysis. Another feature of perfect forward secrecy is that it prevents coarse-grain playback of traffic. Once the clock-based master key has been updated, traffic encrypted or authenticated with the help of old keys will be rejected by SKIP.
SKIP uses the long-term secret key Kij and the date/time value n to create a time-based shared secret key Kijn.
Kijn = h(Kij, n) |
where h is a pseudo-random function such as MD5. SKIP uses the current time and date clock (actually, the number of hours since 1977) to generate n, which changes every hour. Consequently, hosts using SunScreen SKIP must verify that the date, time, and time zone settings on their systems are synchronized to ensure that they are using the same n in their master key calculations.
This time-based shared secret key is used to encrypt traffic keys. Since I and J can calculate Kij based on their implicitly authenticated shared secret, the two computers can calculate the same value for Kijn if their system clocks are synchronized.
Note -
SKIP relies on the system clock value to calculate time-based shared secrets. Consequently, hosts using SunScreen SKIP must verify that the date, time, and time zone settings on their systems are correct to ensure that they are using the same n in their master key calculations. Users should never change the time, date, or time zone setting on their computer while using SunScreen SKIP.
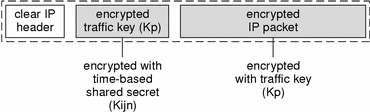
When I wants to send a secure message to J, I uses a randomly generated traffic key Kp to encrypt the contents of the message. The traffic key Kp is in turn encrypted using Kijn. SunScreen SKIP then constructs a series of packets, each containing the IP header information (in cleartext) needed to route the packet to its destination, the traffic key encrypted with the time-based shared secret Kijn, and the message data encrypted with the traffic key Kp. The following figure shows an encrypted IP packet, using this two-step encryption procedure.
Figure B-6 Encrypted IP Packet
When the destination host receives this encrypted packet, it looks up the sender's certificate. Using the long-term secret key Kij and the counter value n (which is based on the current date and time), the destination host computes the same Kijn value used by the sender. Using Kijn, the destination host decrypts the traffic key Kp, and then uses the traffic key to decrypt the packet data.
Since Kijn can be cached for efficiency, SKIP can change traffic keys very rapidly without incurring the computational overhead of a public key operation. SKIP changes traffic keys after a key has been idle for a user-specified number of seconds (30 seconds by default) or after a key has been used to encrypt a user-specified amount of data (512K by default).
Encryption Algorithms
The following table lists the traffic encryption algorithms supported by SKIP.
Table B-1 Encryption AlgorithmsSKIP Certificates
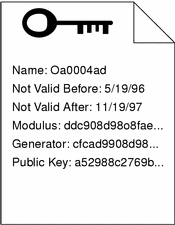
SKIP certificates are the means by which a user distributes public key information. A SKIP certificate is a digital document that contains a user's Distinguished Name, the public key associated with that Distinguished Name, and the time interval for which the certificate is valid. You can distribute your public certificate to other users, who extract and use your public key to calculate a unique shared secret for encrypting communications between you. Users can distribute their certificates freely to other SKIP users on diskette, through a certificate server, or over a network.
Figure B-7 SKIP Certificate Contents
SKIP certificates can be signed or unsigned:
Signed SKIP certificates (RSA certificates) must be obtained from a Certification Authority, which is an entity trusted to create and assign SKIP certificates. In addition to the information described above, a signed certificate contains the name of the certification authority responsible for issuing the certificate and the MD5 hash of the certificate. The CA signs the certificate by encrypting the hash with the CA's private key. The CA's digital signature lets anyone who receives the certificate validate its contents and verify that an unauthorized user is not impersonating you.
You can store signed certificates in directory servers, transmit them by means of non-secure message exchanges, or distribute them on diskette. For information on how to obtain signed SKIP certificates, contact carequest@sun.com.
Unsigned SKIP certificates (unsigned Diffie-Hellman (UDH) certificates) are generated on demand by the user. A user's unsigned certificate can be distributed through secure out-of-band channels or through certificate discovery (which is described on "Certificate Discovery"). Unsigned certificates can offer several advantages over signed certificates:
A user generates a private key when he or she generates a public certificate. This private key never leaves the user's machine, meaning that a network administrator does not need to order, distribute, or protect key diskettes.
Since UDH certificates are not registered by a certification authority, they do not need to be formally revoked. If a user or administrator suspects that a key has been compromised, a new key/certificate can be generated and the new certificate can be distributed to other users.
The decision whether to use a signed or unsigned certificate depends on the type of hosts with which you want to exchange encrypted traffic. In general, you must use a signed certificate to communicate securely with a host using a signed certificate, and you must use an unsigned certificate to communicate securely with a host using a UDH certificate. Both certificates must use keys of the same length and use the same values for key calculation.
Certificate Discovery
Certificate discovery lets a host running SunScreen SKIP retrieve a public (X.509 or UDH) certificate from another SKIP host over a network or serial connection. Certificate discovery is an alternative to direct installation of certificates.
Certificate discovery works as follows:
You verify that certificate discovery is enabled on your computer and on the remote host.
You obtain the identifier and name space of the certificate you want to discover from a remote user by means of a channel that lets you authenticate the other user's identity. For example, you might call a user with whom you want to send encrypted traffic to exchange certificate identifiers and name spaces, relying on recognition of the other user's voice to authenticate the user's identity.
You enter the identifier of the remote certificate in skiptool.
Your computer sends a Certificate Discovery Protocol request to the remote computer in clear text on UDP port 1640, asking for a specific certificate using the designated name space. The remote computer sends back the requested information in clear text on UDP port 1641.
SunScreen SKIP validates the certificate. For signed certificates, SunScreen SKIP uses the Certifying Authority's public key to decrypt the certificate digest, creates its own MD5 digest of the public certificate, and compares the result. For unsigned certificates, SunScreen SKIP creates an MD5 hash of the certificate's public key and compares it to the certificate's name.
SunScreen SKIP adds the certificate for the remote host to its certificate database.
SunScreen SKIP uses the public key information contained in the remote host's certificate to generate a unique shared secret.
Name Space Identifiers
Name space identifiers (NSIDs) identify the type of keys being used. SunScreen EFS 2.0 supports the following NSIDs:
NSID 0, which specifies that the IP address of the host is the key identifier for the host's X.509 certificate. Using NSID 0 results in a small improvement in encryption/decryption efficiency, since SKIP does not need to include a key identifier in each packet.
NSID 1, which is the IPv4 address assigned to the X.509 certificate by a certification authority. This IP address does not correspond to the IP address used by your computer. Rather, it is an eight-byte hexadecimal number assigned to the certificate by the certification authority to bind a unique Distinguished Name to the certificate contents. For example, a SunCA certificate might use 0a000101 (which translates to 10.0.1.1 in IP address notation) as a key identifier
NSID 8, which is the MD5 hash of the certificate's Diffie-Hellman public key.
SKIP Tunnels
A SKIP tunnel is a logical connection between your computer and another host that accepts encrypted messages on behalf of a remote host. Before your computer sends a message through a SKIP tunnel, it encrypts each packet and adds an IP header that specifies the security proxy as its destination. The security proxy decrypts each packet and uses the IP header of the decrypted packet to route the packet to its actual destination.
SKIP tunnels offer several advantages over endpoint-to-endpoint encryption:
Centralized decryption - By directing network traffic through a SKIP tunnel to a special gateway, your site can centralize encryption and decryption in a single machine. Consequently, a site would not need to install security software on every host.
Topology hiding - The tunnel address field contains the IP address of the security proxy; the IP address of the packet's actual destination is encrypted along with the rest of the packet. Consequently, an unauthorized user cannot glean information about a site's topology from a captured packet.
Prevention of packet fragmentation - When using endpoint-to-endpoint encryption, packets may become fragmented as they travel from one site to another. If this occurs, the packet fragments may be routed to different gateways at a site. Since each gateway would receive only part of the packet, the packet could not be decrypted, making it impossible to forward the packet contents to the destination host. By specifying the security proxy to which all packets (and packet fragments) should be delivered, you ensure that the security proxy will receive the information it needs to route packets to destination hosts reliably.











